What is IT Asset Management?

IT Asset Management is a process in which all of a company’s IT resources are effectively identified, inventoried, managed, and optimized. This includes hardware such as computers, servers, and network devices as well as software licenses and digital content.
An example of IT Asset Management is when a company uses a central database or system (CMDB) to track all its IT assets (configuration items), including their configurations, maintenance plans, and license information.
Both worlds (IT and non-IT) of asset management benefit from each other. Through joint planning and effective management, organizations can reduce costs, increase efficiency and productivity, and ensure they have the resources they need to achieve their business goals.
The protection requirements analysis in the ISMS is an important part of IT Asset Management. It helps to prioritize IT assets and thus determine an appropriate level of security for IT resources. A top-down approach is recommended: starting with management processes, through core processes to supporting processes, primary assets are identified first and then the supporting secondary assets are determined. Further “down” in this asset structure, elements of the existing CMDB can then be integrated if required.
Your benefits from IT Asset Management

Optimizing the use of resources

Improved compliance

Increased security

Cost control
What is an asset?
Assets are information values that represent a potential or actual value for an organization and are used in the context of business activities.
An asset is therefore any financially valuable component that can contribute to the provision of an IT product or IT service. A distinction is made between primary and secondary assets.
Primary assets comprise all values and processes that contain information and must therefore be protected. Primary assets can be established processes or know-how, but also physical objects such as documents, prototypes, or models. Purely digital assets are also possible (files, databases, etc.). The actual value lies in the primary asset.
Secondary assets, on the other hand, refer to systems (logical and physical), digital components, inventory items, or similar that are required for the processing, storage, or provision of primary assets. These can be servers, applications, or data centers, for example.
What is asset management according to ITIL®?


According to the ITIL® handbook, asset management is a best practice that encompasses the acquisition, operation, maintenance, and disposal of the organization’s assets, especially those of critical infrastructure.
It therefore refers to the management and optimization of a company’s assets, whether physical or financial, in order to maximize their value and minimize risks. It covers areas such as procurement, use, maintenance, tracking, and disposal of assets.
What types of asset management are there?
Asset management is divided into two main types in the field of information technology: ITAM (Information Technology Asset Management) and SAM (Software Asset Management)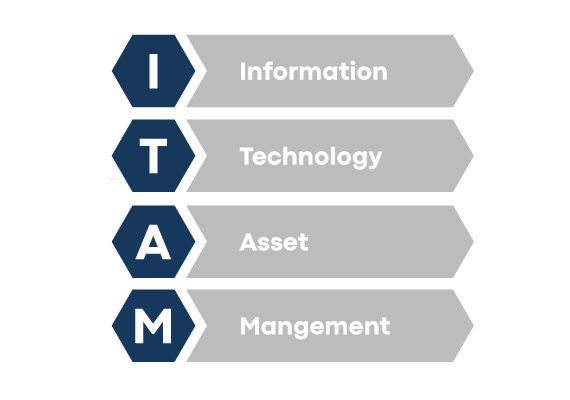
Information Technology Asset Management | ITAM
ITAM refers to the management of all physical and non-physical IT resources of a company. This includes hardware such as computers, servers, network devices, but also software licenses, digital content, and other technological assets. The main objective of ITAM is to ensure that these resources are used, monitored, maintained, and updated efficiently.
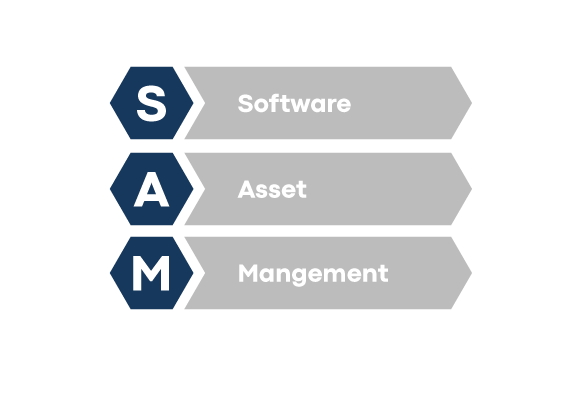
Software Asset Management | SAM
SAM focuses specifically on the management of software licenses and applications in a company. The aim is to ensure that companies have the right number of licenses, are using them properly and that the software complies with legal requirements. SAM also includes monitoring software usage, identifying licensing options, and optimizing software expenses.
Both types of asset management are closely linked and, in combination, ensure comprehensive control over a company’s IT resources. While ITAM covers the entire IT infrastructure, SAM focuses specifically on the software component. Together, they help to control costs, increase efficiency, improve compliance, and ensure the security of IT systems.
The leading software solution for IT Asset Management.
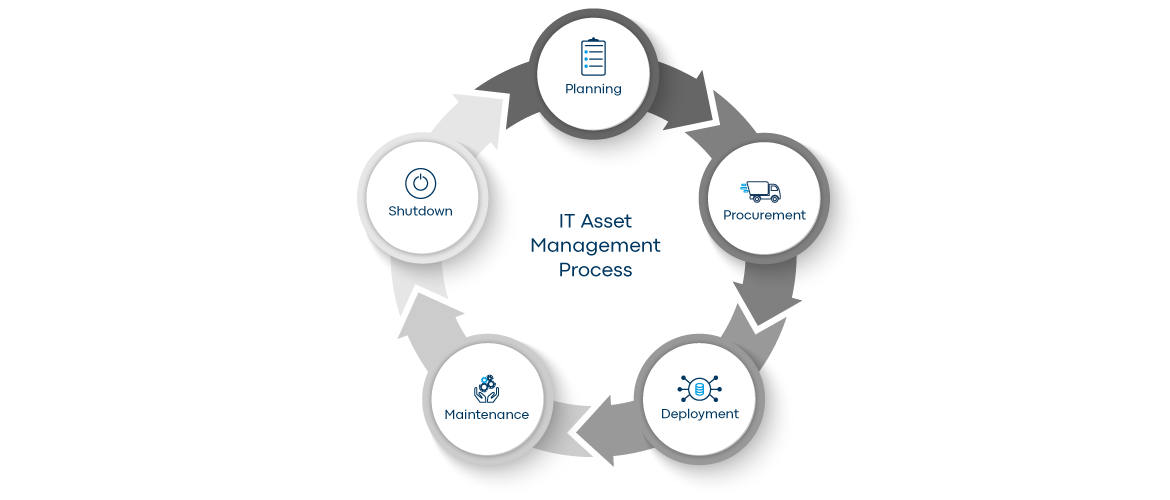
The IT Asset Management process
IT asset lifecycle management is the process of effectively managing IT assets throughout their lifecycle, from procurement to shutdown. The IT Asset Management process consists of several phases, each of which comprises specific tasks:
Planning: In this phase, the objectives and requirements of IT asset management are defined. This includes the definition of guidelines, the identification of responsibilities, and the establishment of processes for the management of IT resources.
Procurement: During this phase, the required IT resources are identified, procured, and made available. This includes the selection of hardware, software, and other technology assets according to business requirements.
Deployment: This is where the procured IT resources are integrated into the IT infrastructure and put into operation. This includes the installation, configuration, and implementation of hardware and software in accordance with the specified requirements.
Maintenance: In this phase, the IT resources are continuously maintained and supported to ensure their performance and security. This includes regular updates, patch management, troubleshooting, and technical support.
Shutdown: At the end of their life cycle, IT resources are decommissioned and removed from the infrastructure. This includes the proper disposal or reuse of hardware, the return or termination of software licenses, and the archiving of data in accordance with the applicable guidelines and regulations.
These phases form a continuous cycle in IT Asset Management and enable companies to effectively manage and optimize their IT assets and minimize risks while supporting their business objectives.
What is a protection needs analysis?

The protection requirements analysis is used to allocate protection requirements for each individual asset in a structured manner. Economic efficiency must always be taken into account, as too little protection entails risks, while overprotection causes unnecessary costs. Protection requirement analyses are carried out regularly, as the assessment criteria or the initial situation can change over time. For example, new compliance or legal requirements may apply, new processes may be introduced or new technologies may be used that have an impact on existing assets.
The aim of the protection requirement analysis in OMNITRACKER Asset Management is now to interrupt the strict inheritance of an overly expensive protection requirement by, for example, fulfilling requirements that selectively reduce the protection requirement: The role and authorization concept of an OMNITRACKER application can, for example, ensure "very high" confidentiality, as unauthorized access is prevented based on the logged-in role. A further inheritance of "Very high" confidentiality to other supporting assets below the OMNITRACKER application is therefore not necessary.
Primary protection goals | Basic protection goals
The primary protection objectives of confidentiality, availability, and integrity must always be evaluated for each asset.Confidentiality
Confidentiality means that sensitive information is protected from unauthorized access. This aims to ensure that information is only accessible to authorized persons and cannot be viewed, copied, or modified by unauthorized third parties. Confidentiality is often ensured by encryption techniques, access controls, and other security mechanisms.
Availability
Availability refers to the fact that information and resources are available to authorized users at all times and within a reasonable period of time. The aim is to ensure that systems and data are continuously accessible and are not impaired by outages, attacks, or other disruptions. Measures to improve availability include redundancy, failover mechanisms, and disaster recovery plans.
Integrity
Integrity means that information remains correct, complete, and unchanged and cannot be manipulated unnoticed. Data must therefore be reliably protected against unauthorized changes during storage, transmission, and processing. Integrity is ensured by mechanisms such as hash functions, digital signatures, and access controls.
ISO standard for ITAM | ISO/IEC 19770

ISO/IEC 19770 is an international standard for IT Asset Management (ITAM) that defines guidelines and best practices for the management of IT resources in organizations.
ISO/IEC 19770 places great emphasis on compliance and license management. Organizations are encouraged to ensure that they comply with all relevant licensing agreements and implement effective processes for license management to avoid over- or under-licensing. Overall, ISO/IEC 19770 provides a framework for implementing effective IT asset management that helps organizations to efficiently manage their IT assets, control costs, ensure compliance, and optimize the performance of their IT infrastructure.
The standard requires an accurate inventory and documentation of all IT assets, including hardware, software, and digital content. This includes details such as manufacturer information, license information, location, and condition of resources. The standard specifies that organizations should develop clear policies and procedures for ITAM, including the identification of responsibilities, processes for recording, and tracking IT resources and guidelines for data security.
Satisfied OMNITRACKER users
OMNITRACKER makes processes clearer and easier.Your software solution in just 5 steps.
Send us an individual enquiry according to your needs.Relevant information on the topic of IT Asset Management
Technical article Protection needs analysis
Our authors show how organizations can sensibly cluster assets and assess their protection requirements, what advantages this brings and what requirements a software solution used for this purpose should meet.
Recording of the live session
In this live session, Andreas Chlebnicek and Jakob Steudel will show you which software-supported methods you can use to carry out protection requirement analyses in your company more efficiently and in line with your needs.